Everyone is talking about critical infrastructure (KRITIS) – and so are we.
Never before have the demands for increased security and digitalization of critical infrastructures (KRITIS) been as great as they have been since this year. As the German government writes in its KRITIS Dachgesetzt: “The range of critical infrastructures is wide, the dangers are manifold and range from human error, terrorism and sabotage to an inadequate supply of necessary resources, e.g. due to the collapse of supply chains…”
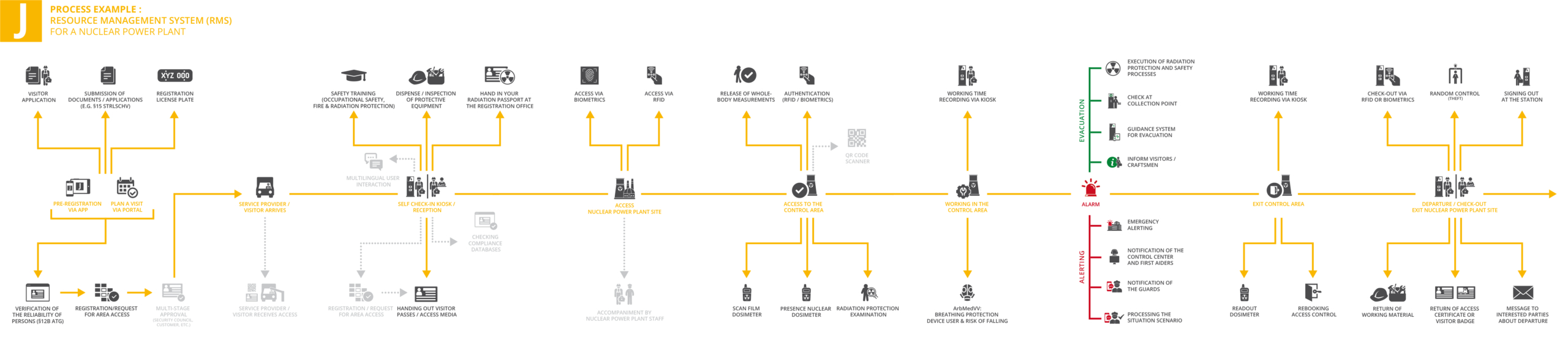
These dangers and challenges must be countered. This presents companies with considerable challenges, e.g. when converting their digital infrastructure. It’s a good thing that we have the JAMES process management software, which not only allows us to map various processes such as reception at the gate through to the control of logistics processes, but also offers an omnipresent focus on security.
Our visitor management solution JAMES is a software that has grown in practice. Over time, the diverse needs of a wide range of customers from various industries have led to “creative misuse” of modules and functions. Due to constantly changing challenges and user demand for ever more specific functions, JAMES has evolved from a visitor management software to a holistic process management solution. JAMES thus combines functions such as visitor and contractor management, resource management, alerting and evacuation, connection to electronic security systems and access control in a single software solution.